In this digital era, where technology is an important part of our lives one should always look out for digital dangers and online scams. Just like when one go on a trip and makes sure to have all the necessary tools and things similarly Cyber security is your armor, ensuring that you can explore the online world without falling into any danger and leaving your digital footprints at vulnerable sites.

Cyber security deals with computer related and content related crimes.
Types Of Cyber security
5 types of cyber security are –
Network Security
It a type of cyber security that secures the communication channels and infrastructure that are used to connect different devices and systems. Technologies involved in network security are : firewall, intrusion detection systems (IDS), intrusion prevention systems (IPS), and virtual private networks (VPNs).
Cloud Security
Cloud security provide security to our all those data and activities which happen at cloud platform like uploading our photos, videos and different media files on cloud storage like google drive, one drive etc. It involves authentication, encryption, and access control measures to ensure the confidentiality and integrity of cloud-based resources.
Application Security
Daily we used to download different applications and software on our mobile and computers, these application sometimes also contain malware and different vulnerabilities which risk our personal data. So Application security is type of cyber security which focuses on identifying and addressing vulnerabilities by secure coding practices, regular code reviews, and application level firewalls are used to minimize the risk of exploitation.
Data Security
It involves protecting our personal data from unauthorized access, disclosure or alteration. It uses different techniques to safeguard data like . Encryption, access controls, data masking, and data loss prevention (DLP).
Mobile Security
Mobile security type is dedicated to securing mobile devices and the data store on it or access. Mobile device management (MDM) and mobile application management (MAM) are some of the techniques used for mobile security.
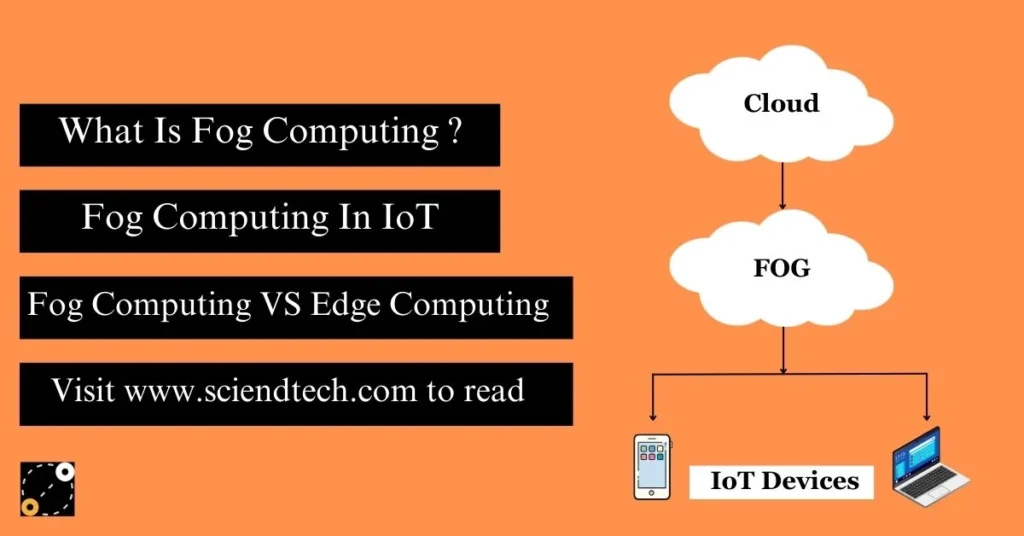
Internet of Things (IoT) Security:
IoT security deals with the protection of connected devices and networks in the Internet of Things ecosystem. It addresses vulnerabilities in IoT devices and ensures secure communication between devices and the central network.
what are the three goals of cybersecurity
Three goals of cybersecurity are :
- Confidentiality
- Integrity
- Availability
Confidentiality
Confidentiality is one of the most important goal of cybersecurity. It ensures that personal information or sensitive data of user remain confidential to the user only or to the authorized entity. Encryption play very important role in maintaining confidentiality.
Integrity
It focuses on maintaining trustworthiness of the system and prevent unauthorized changes in the personal data. Many techniques are used for maintaining integrity of the system like : Digital Signatures, Checksums and data hashing.
Availability
Cybersecurity keep trying to ensure that systems services, and data are easily accessible to authorized users when needed. It gives protection against the DOS attacks (Denial Of Service Attacks).
Content related crimes
- Hate speech
- Malicious content
Computer related crimes
- Hacking i.e. unauthorized access
- Phishing in cyber security
- Spamming
- Spoofing
- Money Laundering
- Cyberstalking

Cyber Terrorism
It involves state vs non-state actors and it is use of cyberspace to put pressure on government and people so as to achieve social political goals.
It uses methods like :
- DDoS
- Propaganda
- Cyber Attacks
- Attacking the privacy of the citizen.
Cyberwarfare
- It is state versus state.
- Use of cyberweapons like Stuxnet used by US and Israel against Iran’s Natanz nuclear facility.
- Cyber espionage – surveillance to gather intelligence.
- DDoS attack – Distributed Denial of Service attack. Ex – Russia targeted the Banking system of Georgia.
Social Media based terrorism
Use of social media sites by terrorist organizations. Social media sites is new media as is based on internet. It has better reach, and faster. Before 9/11 terror attack on the United States of America, world used to see terrorism as a local issue.
After 9/11 United States of America became leading country in war against terror with operation enduring freedom in Afghanistan. After this terror organisations were suppressed and found it difficult to operate. After the US Iraq war many transnational terror organisation emerged.
Transnational terror organisation are using social media sites in various ways like for fund-raising, recruitment, creating terror and propaganda. This has also led to grass root terrorism.
Architecture for Cyber security in India
- National Information Board headed by national security advisor reporting to cabinet committee on security. It is apex cyber security organisation of the country.
- National Security Council Secretariat and National technical Research Organisation support NIB. NTRO is the top most technical, spying agency of cyber security in India. One of the objectives of NTRO is to monitor the computerized attacks.
- NTRO (National Technical Research Organisation) is supported by NCIIPC (National Critical Information Infrastructure Protection Centre).
- In 2000 IT Act was brought and amended in 2008 to protect severe Information Infrastructure like Railways, Aviation, Stock market etc. CERT used to handle entire cyber shield but now a new infrastructure in form of NCIIPC is set up specifically for Critical Information Infrastructure.
- NCCC (National Cyber Coordination Center) – it will be generating real time computerized threat information.
national cyber security policy 2013
- CERT (Computer Emergency Response Team) will be nodal agency
- Train 5 lakh cyber professionals
- It also talks about NCIIPC
- Every organisation will appoint computer security officer
- It calls for Public Private Policy
It has been a concern that this policy may not be adequate to deal with latest networked security in India.
Tools for cyber security
- CMS (Central Monitoring System) – for getting information by intercepting electronic message.
- Netra – to collect and collate information
- NATGRID – to have 360 profile of an individual
conclusion
The conclusion that can be derived from this article is that Cyber security is extremely necessary in today’s world due to immense rise in Cybercrimes nowadays such as Hacking, Phishing etc. There are some major Cybercrimes such as Cyber Terrorism, Cyberwarfare which includes terrorist organizations, citizens privacy, etc. Indian government has also taken steps to enhance Cybersecurity such as NCIIPC, national cyber security policy 2013. There are also tools such as CMS, NATGRID and secure indigenous operating system which are used to provide effective Cyber security.
FAQs
What is cyber security in simple words?
Cybersecurity focuses on providing security from computer related and content related crimes.
What are the 7 types of cybersecurity?
Types of cybersecurity are :
- Application security.
- Network security.
- Cloud security.
- Internet of Things (IoT) security.
What is cyber crime in simple words?
These crimes are related to computer, network device or a network it can be phishing, spamming, spoofing and money laundering etc.
What are 5 cyber crimes?
5 cybercrimes are :
- Hacking i.e. unauthorized access
- Phishing
- Spamming
- Spoofing
- Money Laundering